Basic Interview Questions and Answers
Basic Interview Questions and Answers
 |
| Automation Anywhere |
Question: Do I need to finish all my work in one application before moving onto the next application or can I switch back and forth between various applications while recording?
Answer: You can switch back and forth between various applications while recording.
Question: Can Automation Anywhere work if computer is locked? Can I record a task to unlock the computer?
Answer: Yes. Automation Anywhere offers secure Auto Login technology. Auto Login allows scheduled tasks to run even when computer is locked. When you schedule a task you can enable Auto Login capability. If Auto Login in enabled, and if computer is locked, Automation Anywhere will unlock the computer, run the task and lock it back.
Question: I use remote access software to access a remote machine. Can I record a task that performs activities using remote access software?
Answer: Yes. Automation Anywhere supports all the remote access software.
Question: Is it possible to store special characters like Tab key in a variable?
Answer: Yes, you can store any special character as a text value in a variable.
Question: Can I get all the file names in a folder to perform some operation on it?
Answer: Yes, you can use the “Loop for Files in a folder; Here $FileName$ will have next filename inside the specified folder in each Loop execution. You can use this System variable to perform any operation inside the Loop – End Loop block.
Question: How do I know if my Script ran without any Error?
Answer: You can use the ‘If Script Successful’ subcommand inside the ‘If command’. This command will run the script and will execute the ‘If – End If’ block only if the script ran successfully.
Question: When I use ‘Run Task’ command, how do I know if the task successfully completed?
Answer: You can use the ‘If Task Successful’ subcommand inside the ‘If command’. This command will run the task and will execute the ‘If – End If’ block only if the task ran successfully.
Question: Is it possible for me to know if one of my software is running or not? I want to do certain action only if that software is running.
Answer: Yes, you can use If Condition (If Application Running) to see if any application is running or not. You can specify the exe name that you want to test in the If condition.
Question: What is a Clipboard and its functionality in Automation Anywhere?
Answer: A Clipboard is a special variable which stores the value of system clipboard (Ctrl+c). We can utilize clipboard subcommands like Clear Clipboard, Assign to Clipboard, and Assign from Clipboard to variable clipboard value.
Question: What are the features will carry forward when we deploy a task in AA control Room?
Answer: Properties of the respective task will carry forward to control room when we deploy a task, Unlike Schedule and Triggers will only restrict to Developer Client.
Question: What is the difference between Email Automation Command and Send Email command?
Answer: Using Email Automation Command we can automatically manage the email messages such as manage your incoming emails and extract attachments to specific folder, clear unwanted email messages, communicate your email server and monitor email activity etc. But, send email command we can trigger the emails and include the attachments with it and format the message in HTML.
Question: What is Auto Login?
Answer: Auto Login automatically unlocks and log into a computer while running an automated task means auto-login option allows you to run tasks on computers that are unattended. Auto-Login unlocks the computer, and runs the automated tasks, and returns the computer to the original state.
Question: What is a hotkey and how we assign a hotkey to a task in AA?
Answer: A hotkey is a shortcut key we can use to run the task in Automation Anywhere Enterprises Client (AAE Client). In AAE Client to assign a hotkey select task–>properties–>hot key.
Some more Basics of Automation Anywhere
Some more Basics of Automation Anywhere
 |
| Automation Anywhere |
Question: What is the difference between Object Cloning and Smart Recorder?
Answer: Smart recorder uses object cloning as an underlying technology, so there is no difference. But object cloning is more efficient since it can be used where dynamic changes in the screen may occur.
Question: How to get Cell color in Excel?
Answer: You can use VBScript, Macros or Metabot to achieve this. In AA there is no commands to retrieve/identify the color.
Question: Is it possible to share session from child to parent in Terminal Emulator?
Answer: No
Question: How to Work with same title with different windows?
Answer: If there are multiple windows with same window title, AA will list down all the window titles in the respective command. So during task creation, you need to find out which window title (from the command dropdown) is pointing to which window. Once you set the command accordingly it knows which window need to pick-up during runtime.
Question: Can we change the size of an array in Automation Anywhere?
Answer: We cannot change Array size, row or column or both at runtime, if we define an array using Value option. If we select other options like from CSV, from excel, or Database, then no need to initialize size of the array, it will automatically initialize based on file's data. We can reinitialize an array using a file only, on that case only, size of array an changes runtime based on file's data.
Question: How to work with HOVER type menu items?
Answer: Using Manage web control command or web recorder.
Question: How many types of data can extract from websites?
Answer:
- Regular - Unstructured data that has no repetitive patterns.
-
Pattern-based - Structured data that repeats a patterns, such as row in a table or a list.
- Table - Data that resides in a table.
Question: What is Bulk Edit command?
Answer: This command is used to edit same type of multiple commands at a time. It is important to ensure that all the selected commands are of same type and enabled. Bulk Edit doesn't work if any of the selected command is disabled. Bulk Edit commands works with Insert keystrokes, Object cloning, Object Properties and Delay.
Question: How to change window title from the task file, if window title is changed?
Answer: Select all the task, right click and click on change windows title option and provide new windows title from the drop down list.
Question: What is the unique identifier for a client in the control room?
Answer: A combination of IP address and application path is the unique identifier for clients in the ctrl room.
Question: Mouse click and mouse move are working with based on?
Answer: Coordination-based
Question: What precautions need to take if the image is not showing while trying to do image recognition?
Answer: We need to adjust the match percentage and tolerance.
Question: What is mean by Surface automation?
Answer: Surface automation typically means virtual automation using screenshots, image recognition, and OCR.
Question: In Web CR, what does the number of active users reflect in Dashboard?
Answer: It states the number of Task editor or Task runner being executed at any particular time.
Question: Automation Anywhere Web Control Room’s Dashboard Component displays the number of registered clients what does this indicate?
Answer: It indicates the number of development environments/ AA Task editors/ Task runners currently using the servers/control rooms features or working as part of client server architecture.
Question: Explain about Automation Anywhere Credential Vault?
Answer: Automation Anywhere credential vault basically gives you the facility to securely store password kind of secure data and use it at run time in BOTS.
These variables can be access through F2/variable only in the places like password field.
Question: Two systems which are having different OS. For one system, AA should do module1 in the task and another system AA should do module2 in the task. How can we resolve this scenario?
Answer: There is a system variable called ‘OS Name’. If OS Name is for the first system, then do module 1 else do module 2.
Question: A string ‘’v1@v22@v3@v4” has to spit as “v1” and “v22@v3@v4”. How can you do?
Answer: Use split string operation and set limit as 2.
Question: How to query the database table when there are no headers?
Answer: In your connection string use HDR=No
Question: What all extensions does PGP support for encryption and decryption of files?
Answer: It can support all types of extensions for encryption and decryption.
Question: Which one of these (properties,trigger,scheduling) are supported for an uploaded task bot on CR?
Answer: Trigger and Scheduling are not supported in the control room, they are only on the local client.
Question: Which one from these two -manual mode /Express is the default mode of credential Vault settings?
Answer: Express mode is Default mode.
- Express Mode - Use this to auto connect to the Credential Vault with the master key that is stored in the system during Enterprise Control Room configuration.
- Manual Mode - Use this to manually connect to the Credential Vault using the master key that was available during Enterprise Control Room configuration.
Question: How can we limit the bots to be scheduled or be in progress in activity for particular day in a week?
Answer: You can schedule a bot to run on a particular day of the week. In the "Schedule bot" screen in the "Schedule + Device" tab, select "Run repeatedly". Under "Repeats" select "Weekly" and then select the day or days you would like the bot to run. You can also add a conditional statement to a bot to check the day of the week and stop the task if it is not the indicated day. There's not a built-in weekday command in AAE but there are a number of way to derive the weekday (database, script, Meta Bot, etc.).
Question: I have a excel sheet with multiple columns and row . How do i loop through particular column based on column header name not column number?
Answer: Using $Excel Column(Column Name)$ works when the "Contains Header" box is checked. This may not be an option for all spreadsheets, such as when there are duplicate header names or blank headers. In such a case, the column headers would be the first row of data. You can then loop through the first row of data by incrementing the column index and assigning the index for the matching column to variable.
Question: How to add config files as a dependency to an existing task file?
Answer: In the AAE Client there is a tab on the right hand side of the task that says Task dependencies, you can add it there.
Question: How can read the csv file data column 1 which start from row number 3 to end of column?
Answer: You can give an If condition using $Counter$ system variable (e.g. If $Counter$Greater than(>) "2" Then) inside the loop.
Question: Can we insert multiple rows at a once using SQL query in AA?
Answer: No.
- Reading variable from database is applicable only for array type variables.
- To access Credential variables during task creation and play, the Bot - Creator has to be online (i.e. connected to the WebCR).
- Only Terminal Emulator command session state can be shared between TaskBot/MetaBot Logics. The existing state is passed on to all Terminal Emulator sub-commands in the subsequent TaskBot (sub-tasks)/ MetaBot Logics.
- Types of delimiter for text file - New Line, Comma, Tab, Other.
- Types of delimiter for CSV file - Comma, tab, Regional List Separator.
- Internet Connection command - Only dial-up connections can be used with this command.
- Regional settings supported - English, German, French, Italian and Spanish.
- The Excel command is only supported for Microsoft Office 2000 and later.
- To reference (include) the file in that particular task it is recommended that you use the System Variable AAApplicationPath$. Note that the dependent files can be added only if they reside in the My Tasks, My Docs, and My Scripts folders. If you choose any other source, the error appears.
- Available filters in Task Editor - Mouse Moves, Keystrokes, Mouse Clicks, Delays, Other (Display or hide all commands from the editor that are not mouse moves, keystrokes, mouse clicks or delays.), Windows.
- Convert If Windows Control Exists: Runs the command if the specified Windows control exists.
- Convert to if Web Control Exists: Runs the command if the specified Web control exists.
- Convert to Prompt: Convert a Keystroke command to a prompt message.
- Convert to Variable: Convert a Keystroke command to a variable.
- Bot Dependencies - This option is available only for TaskBot and not MetaBot Logic.
- You can run automation anywhere using batch file and excel macro as well.
- Automation Anywhere does not store debugging information (Breakpoints); therefore, when exiting application, be aware that all Breakpoint information will be lost.
- Priority for queuing - Specify a priority for the task, which will decide the precedence of the task when it is in a queue. Also, if the priority is same then rules apply for precedence of jobs.
- Timeout - Specify timeout for the task to ensure that the task gets aborted automatically after the specified time. Timeout can be set only in minutes between 0 and 9999. Refer Timeout for more details.
It is also important to note that Timeout for a task is not applicable:
- If the task is run in Debug mode.
- If the task is called through 'Run Task' command. In this case, timeout of the main task will be applicable.
- The speed of the task can be adjusted to run in 3 speeds:
- Standard Replay - The task runs at the same speed as when it was recorded.
- High-Speed Replay - The task runs at a faster speed than was recorded.
- Turbo-Action Replay - The task runs at the fastest speed and excludes any mouse moves.
Automation Anywhere - Control Room
Web Control Room
 |
| Automation Anywhere |
In Web control room session will timeout in 20 minutes after you log in and the session is idle for that time period.
Note: Control Room does not allow multiple sessions to the same account at the same time.
Features of Web control room:
- View task relevant activities.
- View the history, tasks in progress and the tasks and activities carried out in control room.
- Manage the automation (bot) files repository and schedule or run tasks.
- Manage credentials and lockers.
- View and manage the statuses of devices.
- View bot schedule details.
- Manage various work items.
- View recent activities of users and administrators.
- Create new and manage existing roles.
- Manage and configure users (client and administrator), assign roles and licenses
Menu options available in Web CR:
-
Dashboard - Provides exclusive graphical insight so that you can make informed decisions for your Bots. It represents your RPA infrastructure in the form of meaningful visuals and charts so that you can analyze it, interpret it, and take action on updates important to you. It dynamically updates information related to active users, registered clients, failed tasks, apps, bots, bot schedules, workflows, queues, and the overall status of devices - their memory, CPU, and HDD utilization.
- Home -
- Total active users widget - This widget displays the total number of active users in Control Room.
- Total clients registered widget - This widget displays the total number of registered clients connected to Control Room.
- Total failed tasks widget - This widget displays the total number of task execution failure. Last 2 days.
- Total Bots widget - This widget displays the total number of Bots.
- Total Bot Scheduled widget - This widget displays the total number of Bots that have been scheduled in Control Room. Next 7 days.
- Total queues - This widget displays the total number of active queues.
- Bots -
- Bot Heartbeat Widget - The Heartbeat widget provides a statistical representation of the relationship between the failure score of a bot and the respective bot. A failure score is a calculation of the resources utilized by the CPU, memory, and hard disk (HDD) when you run a bot. By default, the formula for calculating the failure score is:
Failure Score = 0.5*M + 0.3*C + 0.2*H
where,
M =Memory usage
C = CPU usage
H = HDD usage - MVP Bots Widget - This widget displays bots based on their maximum processing time and the number of times they are run.
- Top Failure Reasons Widget - This widget categorizes the errors that your bots may encounter into various groups and shows the count of each group.
- Upcoming Schedules Widget - This widget shows all bots that are scheduled to run, which are sorted by the number with which they are run.
- Devices -
- Failure Analysis Widget - This widget displays the top n number of devices with most failures for a given time period.
- CPU Utilization Widget - This widget displays the number of devices that crossed the threshold for CPU usage for a given time period.
- Memory Utilization Widget - This widget displays the number of devices that crossed the threshold for Memory usage for a given time range.
- HDD Utilization Widget - This widget displays the number of devices that crossed the threshold for HDD usage for a given time range.
- Overall Device Status Widget - This widget displays the number of Devices that are Connect or Disconnected for a given time range.
- Upcoming Device Utilization Widget - This widget displays the number of devices on which automations are scheduled to run, offline devices and MvP (most used) devices for a given time range.
- Audit -
- Provides a chart-based view of activities filtered on the Action Type column for a given time period.
- Provides a chart-based view of activities filtered on the Source column for a given time period.
- Provides a chart-based view of activities filtered on the Action Taken column for a given time period.
- Provides a chart-based view of activities filtered on the Action Taken By, Action Type and Source column for a given time period.
- Workload - The workload page allows you can view the status of device pools, queues and work items in the Workload Executive and or Operation Manager’s Dashboard.
- Executive Dashboard - You can Monitor the progress of the queues for which you are the owner and/or consumer.
- Device Pool Blocking - Allows you to view the device pools by backlog.
Backlog = Number of hours it takes to complete the existing work items from all automations in that pool. - Queues by time to complete - Allows you to view the list of queues ordered by time to complete.
Time to complete = Number of hours it takes to complete the existing workitems. - Queues Status - Allows you to view the list of queues that were processed in the last n days.
- Queues with Avg. processing time - Allows you to view the list of queues that were processed in the last n days with average processing time.
- Operations Manager’s Dashboard - You can monitor the queues for which you are the owner, consumer, and/or participant.
- Device Pools by FTE - Allows you to view the pools in the descending order of Full Time Equivalent.
- Pools by decreasing error rate - Views the list of pools ordered by the decreasing error rate.
Error rate = Number of work items failed/Number of work items processed from that pool. - Device pool by Backlog - Allow you to view the device pools by backlog.
- Queues with Avg. wait time – Allows you to view the list of queues that were processed in the last n days with average wait time.
Wait Time = Automation start or resume time processing start time.
- Activity - Viewing activities that are scheduled and are in progress. At the same time, it allows you to view a historical chronology of activities performed on a bot using the Historical Activity page. You can perform the following tasks using this page.
- In progress - Displays a live status of all on-going activities for control room. Depending on you privileges, you can manage one or more automation activities using a pause, or resume operation. By Default, you will be able to monitor and manage all the ongoing automation which has been triggered or scheduled.
- Scheduled - Displays a list of activities that have been scheduled for a later time in an activity table.
- Historical - Chronologically displays a list if all the activities that have occurred. Example - Scenarios where an activity failed to run can be tracked using this page.
- Bots - you can use the Bots module of Control Room to:
- Run and schedule uploaded bots.
- Run bot with queue.
- Export bot files for Business Life-cycle Management.
- Import bot files for Business Life-cycle Management.
- Work with secure and centralized credentials.
- Credentials - This page provides a centralized location for securely creating and storing sensitive information that is included in automation tasks in the form of credentials. All Control Room users can create credentials. Users with Manage my lockers permission can create lockers and users with Administer all lockers can manage all the lockers in the vault.
Benefits of creating credentials and lockers: - Minimizes the possibility of credential fraud.
- Provides an environment to enable improved security.
- Enables businesses to adhere to processes and credential management compliance.
- Offers increased Automation opportunities with secure data/ applications.
- My Credentials Tab - This tab consists the list of credentials created by a user. All users have permission to see their credentials.
Note: In case you have "AAE_Locker Admin" permission, then you are able to view credentials of all the users. - My Lockers Tab - This tab shows the list of lockers that has been created by a user. A locker can only be created by an authorized user with Locker_Admin permission or a user having 'Manage my locker' permission.
Note: Users can see lockers only if they have created them or if they are a member of that locker. - Credential Requests Tab - This tab shows the list of user-provided credential requests sent to a Locker Admin and Locker owner i.e. when a credential is created with attribute as user-provided, all the consumers in the locker receive a request to fill in the credential value.
Note: If email notification setting is enabled and credentials are added to a locker, then all the locker consumers shall receive an email.
Transfer Credential Ownership - Allows you to transfer the ownership of the credential. If locker is assigned to your credential then the ownership can be transferred to any member of the locker. Else it can be transferred to any user in the system. Once the ownership is transferred to another user, the previous owner can no longer access the credentials. Also, only a Locker Admin has permission to transfer credential ownership. - My Bots - This is a repository of all bots created and uploaded by the user.
- Devices -
- My Devices Tab - As a Control Room admin or a user with manage devices privileges, you can view the devices that are registered to your Control Room instance. Devices privileges include View and Manage Bot runners, Bot creators, as well as Create and Manage Device Pools.
- My Device Pool Tab - As a Device Pool admin you can view all devices pools that can be used for work items in workload management. You can also create device pools comprising Bot Runners. If you are a Device Pool Owner / Consumer you can view only those Device pools of which you are the owner or consumer.
- Workload - Workload Management allows you to manage your work items by dividing them into small yet logical modules and processing those simultaneously to ensure your time based SLAs are met and resource utilization is optimized.
As a Control Room admin user, you can manage the work items in your Control Room instance with help of Queues. You can create, update and control the way work items are included in Queues and distributed to Bot Runners that are part of Device Pools.
- Queues - As a Control Room user with queue ownership privileges, you can create queues. Queue is one of main building blocks for Work Load Management. Queue comprise of logical group of work items that are processed for automation by individual Bot Runners from a pool. These work items are loaded from Excel or csv files.
- SLA Calculator - As a Control Room admin user or a user with SLA Calculator privilege, you can access the Service Level Agreement (SLA) calculator page. It allows you to assess how long would it take to process items based on device pool size or how many devices are required to meet your target SLA.
- Audit Log - Audit Log captures and provides read-only records of all the important actions performed by users for Control Room and Client.
Note: By default the time filter Last 24 hours is selected. - Administration -
- Settings -
- General - using this tab you can perform below task:
- Control Room Installation type, access URL, and program files destination folder.
- Website Security & Configuration details, Control Room Users, Database, and Repository details, Deployment settings, and Security details.
- Bots - Used for Version control. You can configure version control from this option.
- Client Application -
- Enable or disable Secure recording.
- Change Product help URLs - Product help URLs allow you to redirect links to Automation Anywhere Support Site or to any Custom URL of your choice. Use this option under AA enterprise Help menu section.
- Configure Device health checks - Device Health check that includes parameters such as CPU, Memory, and Disk usage etc.
- Credential vault -
- Express Mode - Use this to auto connect to the Credential Vault with the master key that is stored in the system during Control Room configuration.
- Manual Mode - Use this to manually connect to the Credential Vault using the master key that was available during Control Room configuration.
- Email - As a Control Room admin, you can opt to send email notifications to other Control Room users when certain activities that affect the users are updated such as user information, account activation/de-activation, TaskBot execution status etc.
- Users - The Users page of Control Room gives a detailed information of existing users. As a Control Room user with user management privileges, you can view, edit, delete, and enable or disable a user. You can also perform other actions, such as delete multiple users, export the list of users in CSV format, refresh the list in the Users table, and show or hide columns in the Users table.
- Roles - This page allows an admin or user with roles permission to perform actions such as: Create, Edit, Delete roles for various features and operations in Control Room. RBAC (role based access control) grants access to users based on the assigned roles and the accessibility provided to the user.
In control room you can see two types of roles:- System- created: These roles are pre-configured during Control Room installation.
- User- created: These roles are created by user themselves and can be customized accordingly.
- Note: If a custom role /user-created role is created with all Control Room permission then it is not considered as a Control Room Admin role. Only system created Admin role has this privilege.
- Licenses - Control Room License page provides detailed information about the current license that is installed. It also gives the Admin user privilege to monitor license details and usage statistics. Therefore, an Admin user can view these details any time and avail information about the number of products purchased, the number of device licenses purchased, and number of licenses that are exactly in use.
- Migration - Use the Migration page to migrate data from a previous Control Room version 10.x to the current version - 11 LTS. You should be a Control Room administrator with View and Manage Migration permission to be able to use the migration tool - Migration wizard. The wizard can be launched anywhere in a browser from Control Room version 11 LTS. You can migrate – Database, setting, roles, data.
Automation Anywhere - PGP, Prompt and Read from CSV-Text Commands
Automation Anywhere - PGP, Prompt and Read from CSV-Text Commands
 |
| Automation Anywhere |
Prompt Command
This command is use to insert a user prompt that requests input from a user when running an automated task.Sub-Commands
- Prompt For Value - This command is use to get any values from the user. Value May Password or value which change frequently. You can encrypt keystrokes when users enter any value. That value assigns to a variable and that variable is used into an automated tasks.

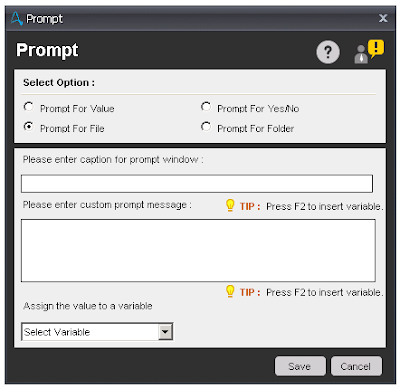
Prompt For Value - Prompt For File - This command is use to prompt the user for one or more files from a single folder. The value of the files selected can be assigned to a list variable.
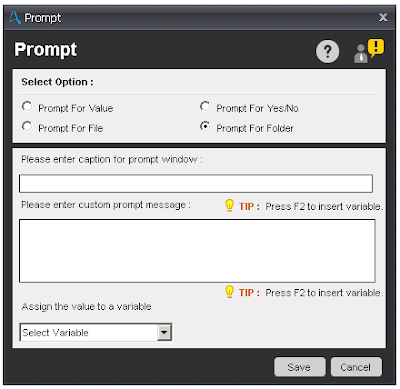
Prompt For File - Prompt For Folder - This command is use to prompt the user for a single folder. The value of the folder selected can be assigned to a value variable.
Prompt For Folder - Prompt For Yes/No - This command is use to prompt the user for a response (Yes or No) to a question while the task is running. The value is selected from the prompt will assign to the variable. This command is basically use for some decision using If/Else command.

Prompt For Yes/No
Read From CSV/Text Command
This command is used to automate the process of reading data from CSV and Text files.Components of Read From CSV
- Select File - Select a CSV file with path which you want to extract data.
- Delimiter - Select the delimiter from the drop-down list to separate the text strings. We have three types of delimiter available to separate text from strings in CSV file.
- Contain Header - Check this box if your file contains the header.
- Trim - This is use to Trim your text.
- Encoding - Select the option from the drop-down list in which CSV is encoded. We have three encoding type available.
- ANSI
- UNICODE
- UTF8
- Session Name - Define the session name to Read the CSV file.

Read From CSV
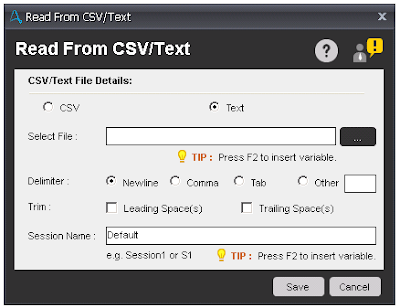
Components of Read From Text
- Select File - Select a Text file with path which you want to extract data.
- Delimiter - Select the delimiter from radio button to separate the text strings. We have four types of delimiter available to separate text from strings in Text file.
- New Line
- Comma
- Tab
- Other - user defined delimiter
- Trim - This is use to Trim your text.
- Session Name - Define the session name to Read the Text file.
Read From Text
Note:- Once you extract text from the CSV/Text, '$Filedata Column(Position of the text)$ ' is use to read data inside the 'Each Row In A CSV/text File' Loop.
PGP Command
This command is use to encrypt and decrypt files from the automated tasks.PGP stands for Pretty Good Privacy.
The command supports both types of encryption: symmetric (passphrase) and asymmetric (public/private keys):
- PGP Passphrase: Requires a pass phrase to encrypt and decrypt.
- PGP Public/Private Key: Requires a PGP public and private key file to encrypt and decrypt.
Sub-Commands
- Encrypt Files
- Decrypt Files
- Create Keys
Symmetric Algorithm available for Encryption/Decryption:
- Idea
- TripleDES
- CAST5
- Blowfish
- AES128
- AES192
- AES256
- Twofish256
Components of Encrypt Files
- Encryption Type - Select type of Encryption whether Passphrase or Public/Private Keys. If you select the Passphrase, then it will prompt to enter the passphrase and if you select Public/Private Keys, then it will prompt to select a file which contains the Key.
- Symmetric Algorithm - Select the type of Algorithm from drop-down list in which you want to encrypt the file.
- Source File(s)/Folder- Select the File(s)/Folder to which you want to encrypt.
- Destination File(s)/Folder - Select the File(s)/Folder path where you want to create encrypted file(s)/folder.
- Overwrite Files/Folder - Check this option if you want to overwrite the file(s)/folder, if exists.
- Append Extension - Check this box and enter extension if you want to change the extension of your file(s).
- Compression Algorithm - Select any option to compress the destination File(s)/Folder.
- Armor Data - Check this option to enable ASCII Armor data.
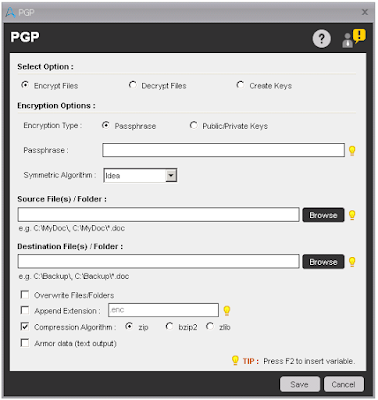
PGP Encrypt Files
Components of Decrypt Files
- Decryption Type - Select type of Decryption whether Passphrase or Public/Private Keys. If you select the Passphrase, then it will prompt to enter the passphrase and if you select Public/Private Keys, then it will prompt to select a file which contains the Key.
- Source File(s)/Folder- Select the File(s)/Folder to which you want to decrypt.
- Destination File(s)/Folder - Select the File(s)/Folder path where you want to create decrypted file(s)/folder.
- Overwrite Files/Folder - Check this option if you want to overwrite the file(s)/folder, if exists.
- Remove Extension - Check this box and enter extension if you want to remove extension from the encrypted file(s).
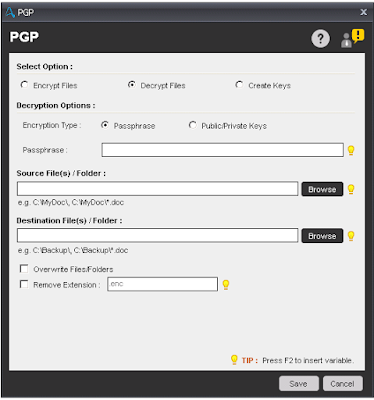
Decrypt Files
Components of Create Keys
- Public Key File - Select the file which contains the Public Key.
- Private Key File - Select the file which contains the Private Key.
- Password - Enter the password, if you want to secure your file with password.
- Overwrite Files/Folder - Check this option if you want to overwrite the file(s), if exists.

Create Keys